This is an old revision of the document!
Table of Contents
Phishing Incident Center Features (threat analyzer)
- Dashboard Filter: LUCY allows you to filter the incoming mails on the dashboard:
- Centralized Analysis: This feature allows you to analyse the incoming mails manually or automatically (see next chapter)
- Centralized Campaign Reporting: Any reported mail which is part of a phishing simulation will be processed within the campaign statistics
- Threat Mitigation: The Threat Mitigation (LUCY 3.5) allows you to take actions against legitimate phishing attacks
- Custom Regex & Score: LUCY allows you to define custom rules to scan mails for specific keywords and flag them with a individual threat score.
Detection of real phishing mails vs. Phishing simulations
The plugin automatically handles emails created in a phishing simulations from LUCY: it will ensure that only reports of potentially malicious emails are delivered to appropriate security staff. All emails created by LUCY itself will create a custom message to inform the user, that the mail has been send as a part of a security awareness program. LUCY generated phishing mails won't be forwarded to the security team. But they will be reported back to LUCY in order to process the information within the campaign statistics. The reported mails will then be purged from the successful attack listings in LUCY.
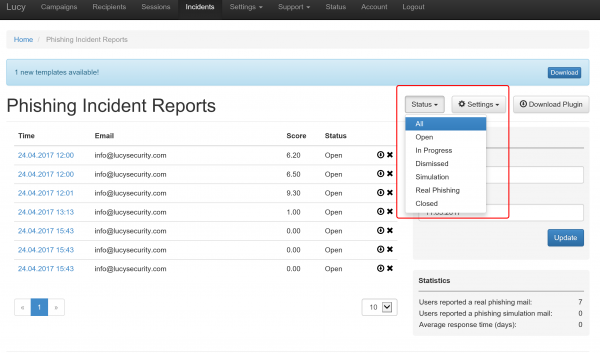
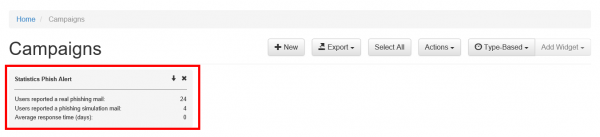
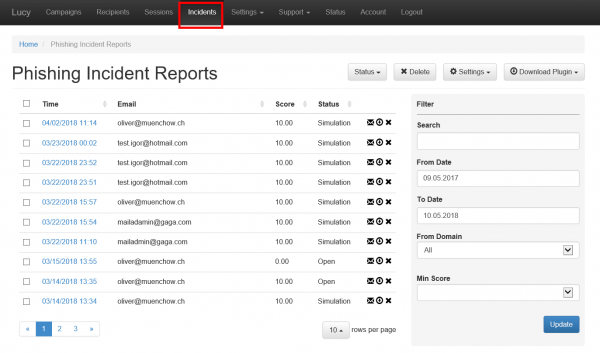
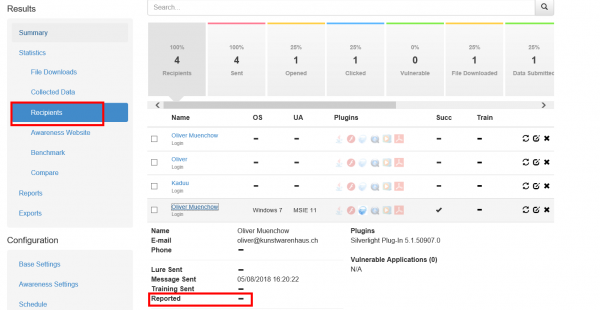
Where are incidents (LUCY generated emails) from the plugin reported?
If a user spots the phishing simulation and reports the email, you can see this information in various places:
- Incident widget on the dashboard:
- Incident tab:
- Under the campaign statistics (recipients) under the "reported" item:
- If you want a comparison of all reported emails, you can export the whole campaign data via CSV. Within the CSV there is a reported column:
In LUCY 4.4, the incidents reports will also be integrated on the dashboard under the general statistics.
Centralized analysis
Once the mail has been reported by the user it will popup as an incident in LUCY in case you have enabled the HTTP option in LUCY. There are a few automatic analysis routines build into LUCY (e.g. check an IP in Google's Safe Browsing Database or Phishtank Database). More checks will follow in the upcoming versions.
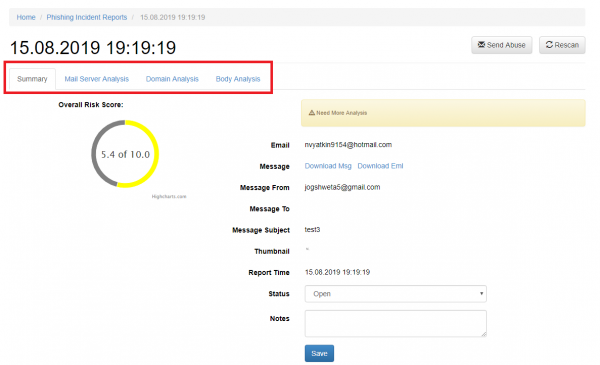
LUCY will automatically flag mail simulations. All other mails can then be manually verified by the administrator. All mails can be downloaded as .msg file and/or add an incident report. When you click on a reported mail you will first see the overall risk score. The overall risk score is a weighted average of the following score from different scans:
- Header Analysis
- Domain Analysis
- Body Analysis
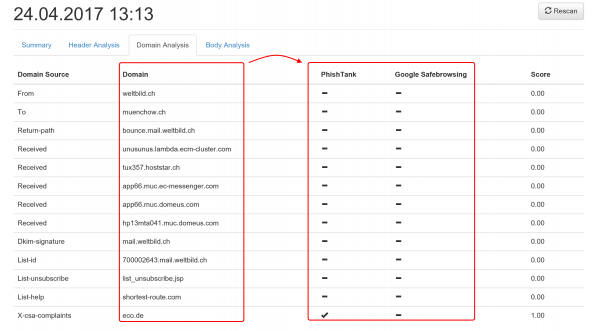
When a user forwards an email to LUCY all the domains and IP's from the mail header & body are extracted. For each IP and domain LUCY will then lookup public databases like google's safe browsing or phishtank, if any threat was reported:
The current sources (LUCY 3.7) are:
- DNS BL queries to bl.spamcop.net and zen.spamhaus.org
- CI Army (list) (http://cinsscore.com/) - Network security Block Lists.
- Palevo Blocklists (https://palevotracker.abuse.ch/blocklists.php) - Botnet C&C blocklists.
- Cybercrime tracker (http://cybercrime-tracker.net/) -
More sources will be added with each new major release. Lucy will query those sources directly from the location where the software is installed. No data is transmitted back to our infrastructure.
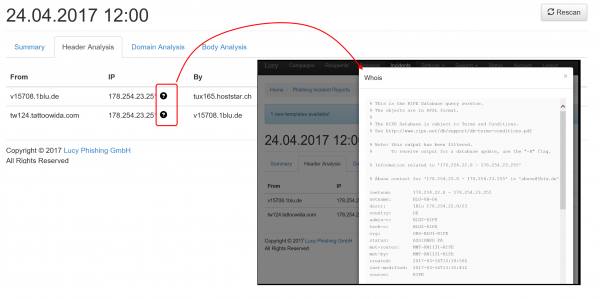
The LUCY admin can also quickly just manually investigate the WHOIS records from the IP's by clicking on the help symbol:
Threat mitigation
The threat mitigation allows a LUCY admin to report reported phishing mails to according abuse contact of the provider's originating IP address taken from the message header. You can click on the mail symbol within the incident center to initiate the sending of the report. More info here.